Categories
What is Phishing?
Phishing is a form of Internet fraud. It consists of swindling people by luring them to a fake (bank) website that is a copy of the real website and having them log in "unsuspectingly" with their log-in name and password or their credit card number. This gives the fraudster access to these data with all its consequences. The victims are often lured to this fake website via e-mail, which contains a link to the (fake) website with the request to supposedly "check the login details".
Method
Phishing often involves the use of URL spoofing. This is mimicking the URL of a bank, for example, so that the user thinks they are visiting the real site, while the URL is that of the imposter.
Since the use of the IDN (International Domain Name) system, which allows non-ASCII characters to be used in domain names, phishing can take advantage of this by mimicking a real domain name with equivalent foreign characters, so that the user does not notice that the address is incorrect.
Even a plain ASCII URL can be cheated: for example, the address www.googIe.com, in which the lowercase l is replaced by an uppercase i (I), looks very similar to www.google.com, and, depending on the font, can even look exactly the same.
Most banks nowadays use an Extended Validation Certificate. In modern Internet browsers, the first part of the address bar is displayed with a green background, so that the user can be sure that he is on the real page.
Usually the victim receives an email asking him to check and confirm his account at a bank, for example. Instant messaging is also used. Sometimes telephone contact is made. Fraudsters frequently use fake sites of financial institutions, eBay and PayPal. Phishing is difficult to detect. Internet users must be especially alert and never respond to an email requesting them to provide personal (financial) information, such as bank account number, PIN number, social security number or credit card details. The first case of phishing dates back to 1996.
How to recognize?
In a phishing message you will often find the following elements:
- The email is not addressed to the customer personally but starts with a general opening like "dear customer"
- The email contains language and style errors
- It suggests that the account should be "verified" with the customer's login credentials
- There is a threat of consequences if the email is not acted upon immediately
A common method is that the fraudster sends an email with an attachment in which a Keylogger is hidden. The email then functions as a Trojan horse. Once the user has opened the attachment, the keylogger is activated in the background. This allows the fraudster to see over the Internet what passwords the user uses when logging into his or her bank.
How to prevent?
- Make sure the computer is well protected with a virus scanner and a firewall. Make sure the operating system, virus scanner and browser are up to date.
- Only do your banking from an account with limited rights (not always possible when additional software needs to be installed).
- Set the spam filter to automatically remove all mail that contains the name of a bank in the sender or subject line. If a bank has something important to say they will never do so by email, so there is no reason for mail from the bank to arrive in the inbox.
Examples of Phishing:
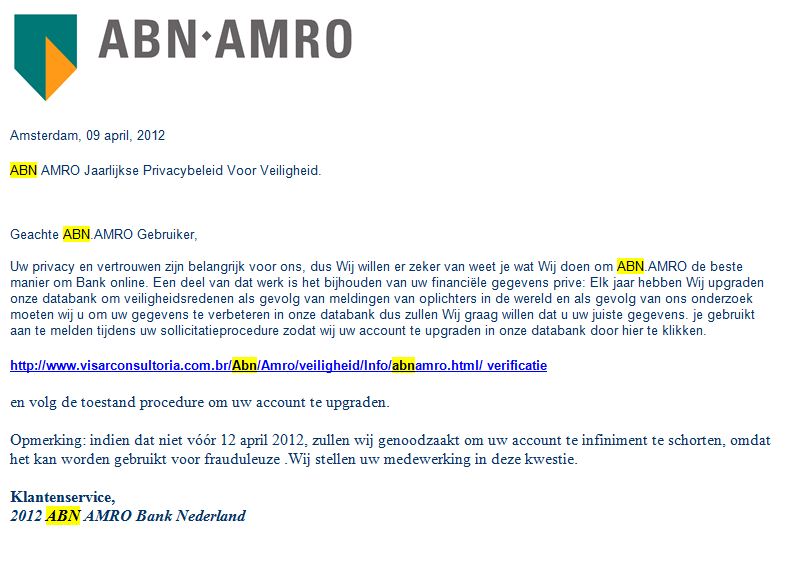
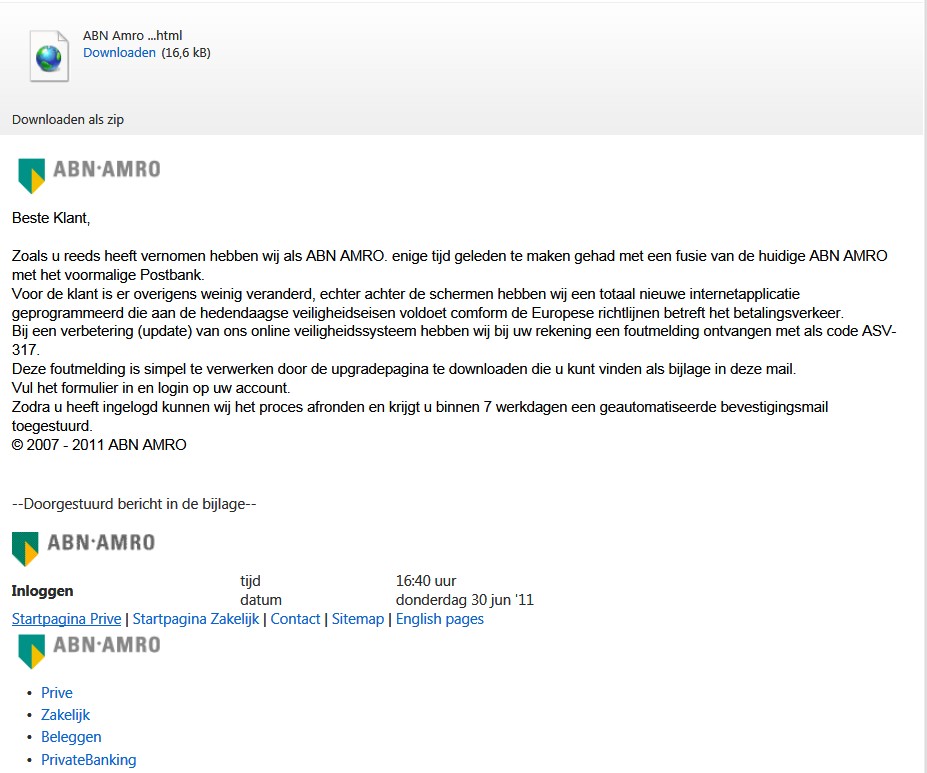
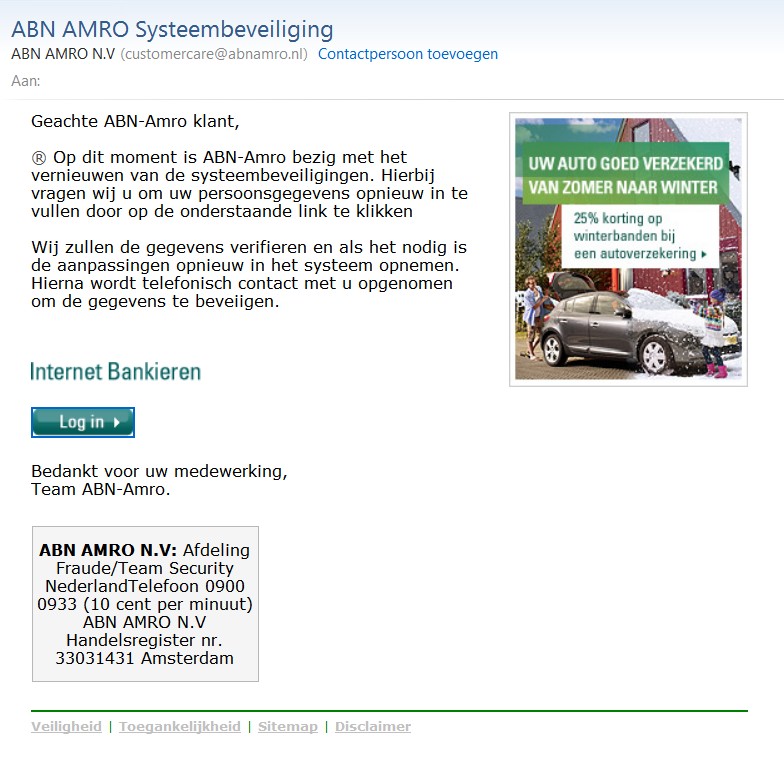
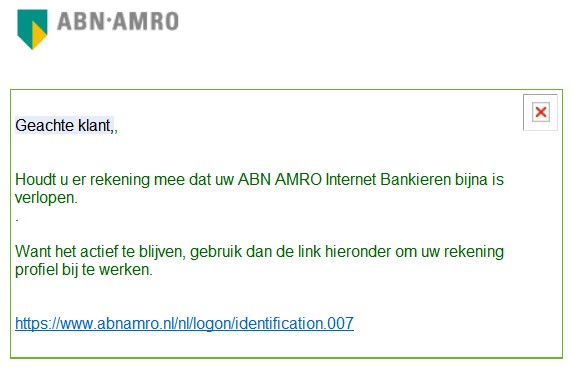

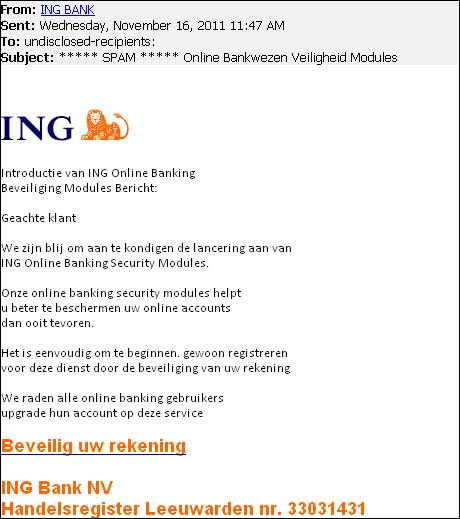
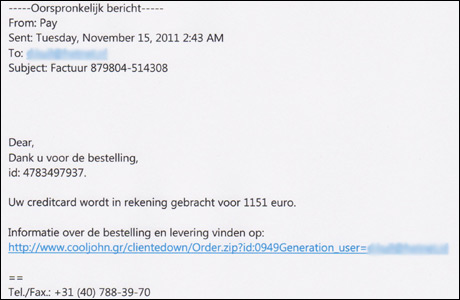




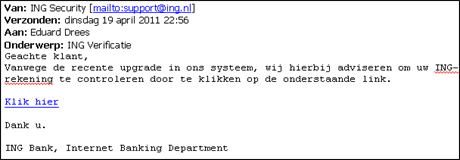
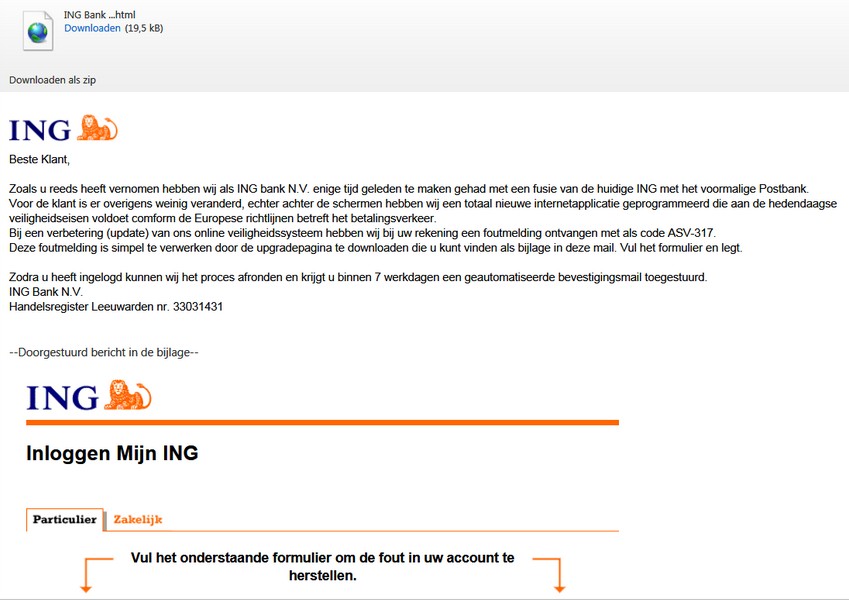
You can also find more information about secure banking and phishing through this link.
Source: Wikipedia